
Our approach to protecting Information has always been focused on securing the digital assets that store, process, and transfer information. With incr...

In today's rapidly changing landscape of cybersecurity threats, Distributed Denial of Service (DDoS) attacks are considered as a formidable challenge ...
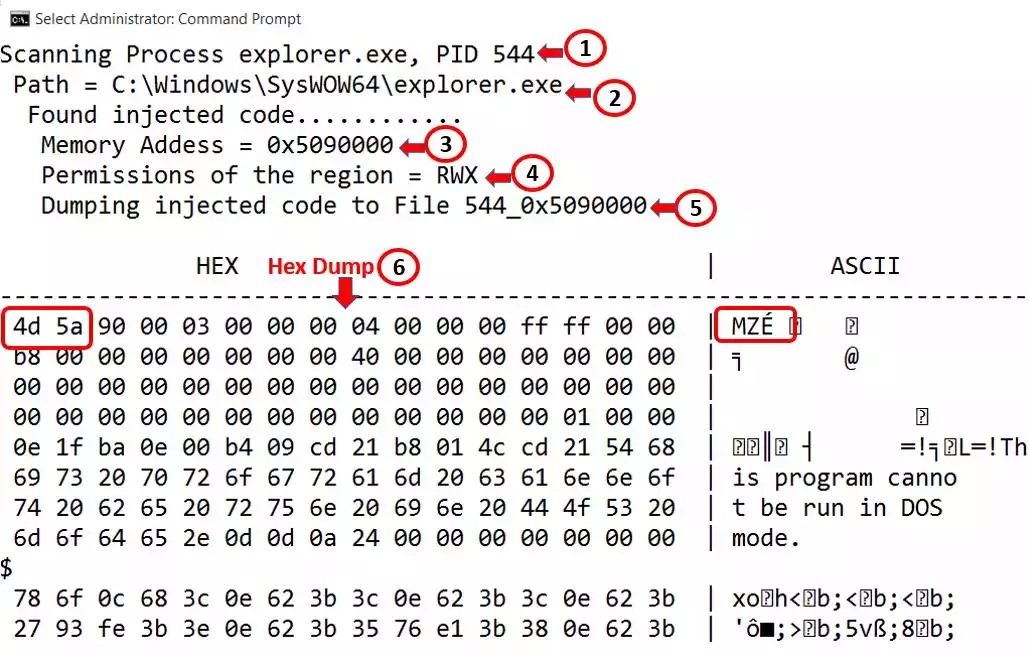
Most of the time threat hunting is initiated by looking at the network logs or IDS IPS logs. But relying only on network logs may be enough as malware...