
Broken access control vulnerability occurs when an application fails to enforce proper authorization checks, allowing users to access resources or per...

Learning from Real-World Phishing Attacks
Understanding the Growing Threat of Phishing Attacks in India and How Simulations Can Shield Your Organization from Catastrophic Losses

RansomEXX targeting Indian Banks
RansomEXX targeted a supply chain unit Brontoo Technology Solutions, a key collaborator with C-EDGE, that provides solutions to the Indian Banking ...

The mutex vaccine for malwares
A lot of malware creates mutex when they are executed on the victim machine. With the presence of the mutex, they ensure that another instance of the ...

A pointer that brought the world to a standstill
A minor bug in a kernel driver of one of the most popular Endpoint Detection and Response (EDR) solutions, CrowdStrike caused a Blue Screen also known...
Snowblind malware hidden threat android banking security
Snowblind, a new banking malware, is a sophisticated and insidious threat designed to exploit vulnerabilities in Android security features. This malwa...

Top eight Malware Types org should defend
Malware, a malicious software, provides cybercriminals with unauthorized access to computer systems. It includes various types of software code, each ...

Ransomware - A Growing Threat to Cybersecurity
In recent years, ransomware attacks have emerged as one of the most prevalent and damaging forms of cyber threats. It is crucial to understand the nat...

Mail bombing overwhelms an inbox with excessive emails, disrupting communication and potentially crashing servers. Preventing it requires spam filters...

Identity theft, a silent menace, involves stealing personal data for fraud. It causes financial loss and emotional distress, emphasizing the need for ...

Comprehensive guide to penetration testing
In the ever-evolving cybersecurity landscape, penetration testing allows you to identify vulnerabilities before malicious actors can exploit them, for...

Our approach to protecting Information has always been focused on securing the digital assets that store, process, and transfer information. With incr...

In today's rapidly changing landscape of cybersecurity threats, Distributed Denial of Service (DDoS) attacks are considered as a formidable challenge ...
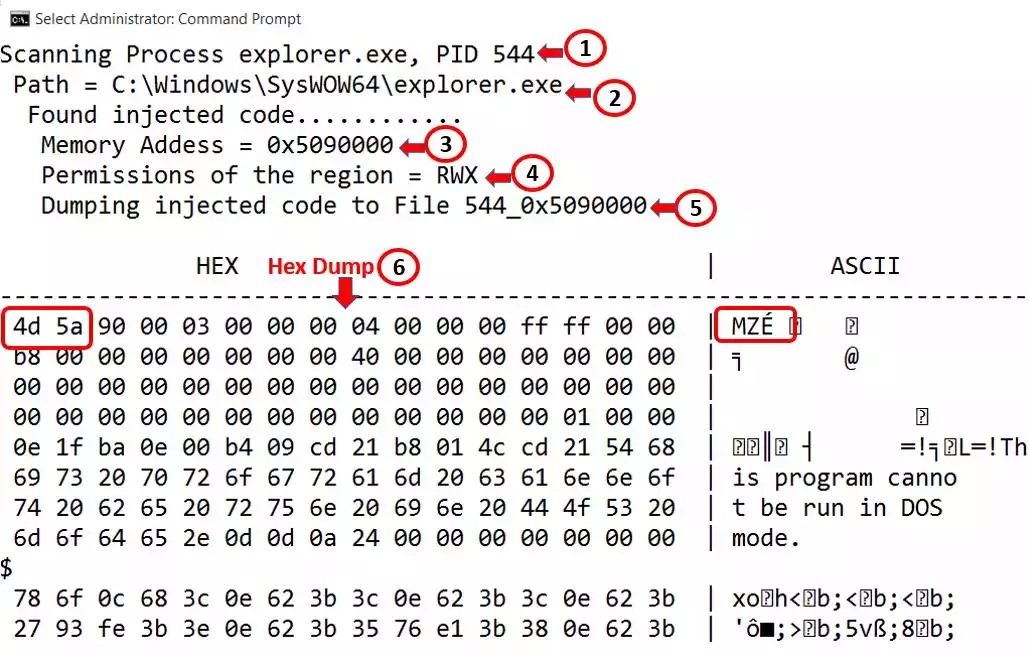
Most of the time threat hunting is initiated by looking at the network logs or IDS IPS logs. But relying only on network logs may be enough as malware...

Learning from Real-World Phishing Attacks

RansomEXX targeting Indian Banks

The mutex vaccine for malwares

A pointer that brought the world to a standstill