7 years ago the spread of Wannacry (version1) Ransomware was just stopped by registering a domain “iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com” . When Wannacry executes on the system it checks for the domain and in case the domain is registered Wannacry stops executing. The domain acted as a kill switch for wannacry. For more details read the link https://en.wikipedia.org/wiki/WannaCry_ransomware_attack .
Fig: from: theguardian.com
It’s not only WannaCry, a lot of malwares check for certain logic before executing the malicious code. Malware prefers executing its malicious code only when it feels it’s a suitable environment. Many malwares do not tend to execute if they are executing virtual machines or if certain tools like procmon, and process explorer running. Malware can also abstain from executing if another instance of the same malware is executing in the system.
Can we use this behavior of malware to prevent it from executing, or in other words blocking its execution?
Most of the deception technologies revolve around setting up honeypots to identify malware activity. Honeypots are created to imitate legitimate vulnerable systems. We can create similar artifacts by modifying registry entries, files, and mutexes on a clean system to make look like a malware-infected system. One of the effective methods of deception is mutex.
A lot of malware create mutex when they are executed on the victim machine. With the presence of the mutex, they ensure that another instance of the same malware does not execute on the same machine. Some malware has a fixed value of mutex while others can create mutex based on the attributes of the victim machine.
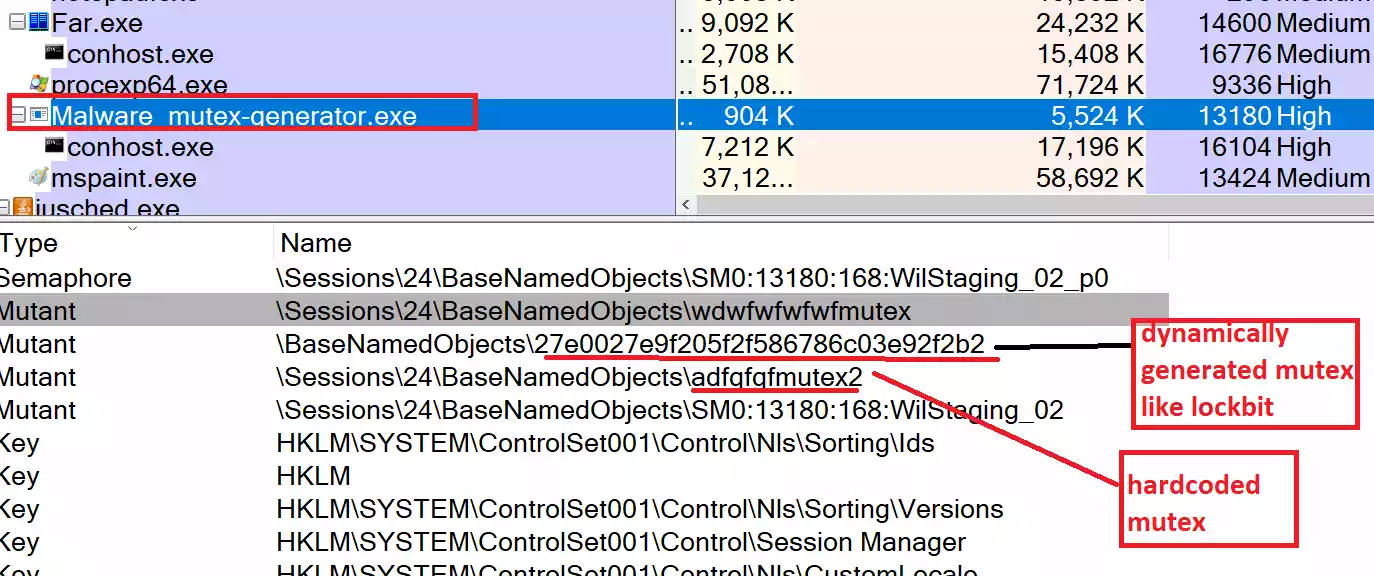
For example, Conti Ransomware Creates a mutex with the name “kasKDJSAFJauisiudUASIIQWUA82” while Lockbit Ransomware creates a mutex dynamically on the victim machine, which is MD4 of the GUID of the victim machine. If you create a persistent mutex in the system, it would act as a vaccine against malware infection.
Here is our code that can generate malicious mutex on the system https://github.com/intelliroot-tech/Mutex-Vaccine.
We collected a list of a few known mutexes from publicly available sources like this: https://github.com/albertzsigovits/malware-mutex.
These mutexes can be hard coded in a file “mutex_names.txt”. The function “createMutexesFromFile” reads the file and creates mutexes. We also added a function “LockbitMutex_Md4Hash” that creates mutex just like Lockbit based on the md4 of GUID of the system. You can add more mutexes and more mutex-generating algorithms to the sample code. The binary generated from the code should be always running in the system so that mutexes stay in the system. If malware comes and checks from the presence of mutex, it will not execute further. We cannot say it would stop every malware, but it can prevent the execution of crucial malware like Lockbit. If this feature can be supplemented with malware-blocking technologies, it would be able to prevent the execution of malware.
At Intelliroot, we develop new technologies that can help the industry combat threats. Contact us if you are interested in similar research topics.

Learning from Real-World Phishing Attacks
August 13, 2024

RansomEXX targeting Indian Banks
August 2, 2024

The mutex vaccine for malwares
August 2, 2024

A pointer that brought the world to a standstill
July 21, 2024